Forget isolated exercises—our platform replicates real corporate environments with live systems, evolving threats, and industry-specific tasks. Train like you’re on the job, master enterprise tools, and prove your skills where it counts.
This is your chance to train like the pros—inside a system that mirrors real-world cyber environments. Whether you’re launching a career or upskilling in your current role, there’s no better way to prepare. Get on the platform and start training today!
Step beyond basic labs into a fully interactive enterprise training platform. Work within real-world corporate IT environments, where systems are interconnected, threats move across networks, and security teams must collaborate to defend them—just like in Fortune 500 companies, government agencies, and critical industries like aerospace, finance, and healthcare.

Unlike typical training, our platform doesn’t reset after every session. Build, break, and secure corporate environments over time. Detect and respond to cyber threats as they evolve, just like a real SOC analyst, incident responder, or security engineer. Learn what it takes to maintain and protect an organization’s digital infrastructure for the long haul.
Customize your training for the industry you want to work in. Protect critical infrastructure in power grids, secure financial transactions, defend healthcare data, or simulate cyber threats in aerospace networks. No generic, one-size-fits-all training—develop skills that directly apply to your target career path.
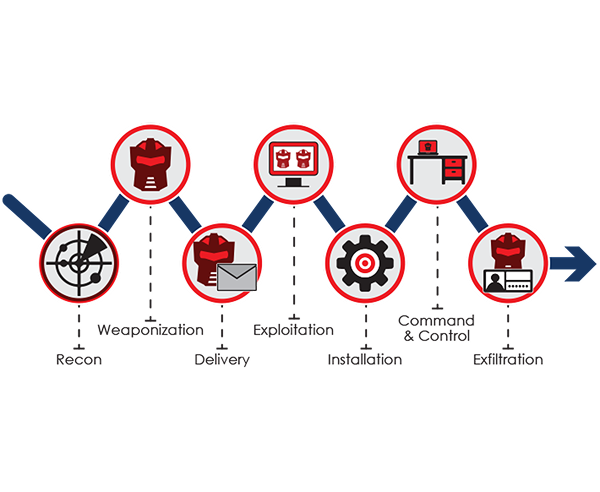
Experience the full scope of cyber threats as they unfold. Unlike isolated lab exercises, our platform lets you see how attackers move through networks, escalate access, and evade detection. Learn to identify, stop, and prevent sophisticated attacks—essential for roles in penetration testing, defense, and corporate security teams.
Knowing you’ve completed a course isn’t enough—our platform ensures you can prove your skills. Every task, from security monitoring to threat response, is tracked and measured against real-world job requirements. You’ll see your progress by skill, role, and industry-specific tasks, giving you a clear roadmap of what you’ve mastered. Employers get detailed insights into learner performance, ensuring they can trust that candidates aren’t just trained—they’re job-ready.

Many training programs focus on isolated exercises, but real-world cybersecurity work doesn’t happen in a vacuum. Our training is built around full systems, real tools, and persistent networks—just like the environments you’ll encounter on the job. You’ll gain experience responding to evolving threats and working within enterprise systems, so when you step into a role, you’re not just familiar with the concepts—you’ve already done the work.
Your Learning, Your Path
New to cybersecurity or upskilling for higher-level roles? Our platform adapts. Task configuration for the job you are looking for. Self-driven skill libraries, guided coaching, and AI-driven recommendations ensure you get the right training, at the right time—never wasting time on unnecessary content.

No One-Size-Fits-All Training
Every learner trains in job-specific tasks, configured for roles like SOC analyst, threat hunter, forensic investigator, and penetration tester. Whether securing power grids, financial networks, or healthcare data, you train on what matters for your job.
Struggling with a concept? Our AI-driven guidance delivers instant job aids, hands-on labs, and walkthroughs tailored to your learning path—without waiting for an instructor. Need expert help? Coaching and instructor-led training are blended in seamlessly.
Show Employers What You Can Do
Every completed task is tracked by skill and job function. Learners see clear progress, while employers get real-time insights into what candidates can actually perform, not just what they’ve studied.


Go Beyond Training—Land the Job
AI-driven mock interviews, resume analysis, and industry-specific job simulations help learners refine their skills for real-world hiring—ensuring they stand out to employers and secure high-value cybersecurity roles.
Trusted By Employers
Companies rely on our platform to build job-ready talent—not just certified learners. Training includes integrated team projects, requiring learners to collaborate in agile environments, practice professional communication, and produce real reports—just like on the job. Whether hiring new talent or upskilling employees, our training ensures learners arrive ready to perform from day one. Our graduates work at 50+ companies, including those below.
© 2019-2025 RapidAscent